The Vault Provider in Terraform
These are some notes from the field around using Vault and Terraform.
Storing a Sample Secret in Vault – Resource vault_generic_secret
provider "vault" {
# It is strongly recommended to configure this provider through the
# environment variables described above, so that each user can have
# separate credentials set in the environment.
#
# This will default to using $VAULT_ADDR
# But can be set explicitly
# address = "https://vault.example.net:8200"
}
resource "vault_generic_secret" "example" {
path = "secret/foo"
data_json = <<EOT
{
"foo": "bar",
"pizza": "cheese"
}
EOT
}Backups of Vault Data
Vault uses Consul as the encrypted database.
consul snapshot will provide the ability to backup the consul db containing encrypted secrets
Authenticate to Vault ( Token Per User )
Users should authenticate to get Vault access. This can happen via github (configure github as the identity provider for Vault). Github will return a token that can be used by each user to authenticate themselves to Vault.
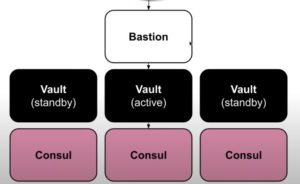
Vault Architecture on AWS (7 EC2 Instances on AWS)
A possible architecture may involve a Bastion host and a couple of standby vault servers. The consul servers should ideally be separate (database servers). This would translate to 7 EC2 instances on AWS.
Need an experienced Cloud Networking or a Cloud Data Protection Expert? Anuj has successfully delivered over a dozen deployments on each of the public clouds (AWS/GCP/Azure) including several DevSecOps engagements. Set up a time with Anuj Varma.
Leave a Reply